Ethereum’s Pectra Upgrade Exploited by Bots Draining Wallets: Report

The feature, meant to improve user experience by allowing wallets to act like smart contracts, has instead been co-opted to drain wallets automatically in what are called sweeper attacks.
Soumen Datta
June 2, 2025
Table of Contents
Ethereum’s recent “Pectra” upgrade introduced several features to improve how users interact with the network. One of the most talked-about changes was EIP-7702, a proposal backed by Ethereum co-founder Vitalik Buterin.
This feature allows wallets to behave temporarily like smart contracts, enabling batch transactions, gas sponsorships, social authentication, and spending limits.
However, according to Wintermute, a leading crypto trading firm, this new upgrade has opened the door to a dangerous wave of automated sweeper attacks, draining unsuspecting users' wallets. And these attacks are spreading rapidly.
A Feature with Good Intentions
EIP-7702 was meant to make Ethereum more user-friendly.
Users could sign just one transaction to handle several actions at once—something previously only possible through smart contracts. For instance, a user could approve a token, swap it, and send the output to another wallet in one go.
It also offered quality-of-life improvements like sponsoring gas for someone else, or using social login systems to authenticate wallets, making it easier for mainstream users to interact with Ethereum without wrestling with seed phrases.
But what was designed to help users has quickly been turned into a weapon by bad actors.
The Rise of CrimeEnjoyor: A Copy-Paste Attack Vector
Wintermute recently published an analysis showing how EIP-7702 is being used by bots in what are called sweeper attacks.
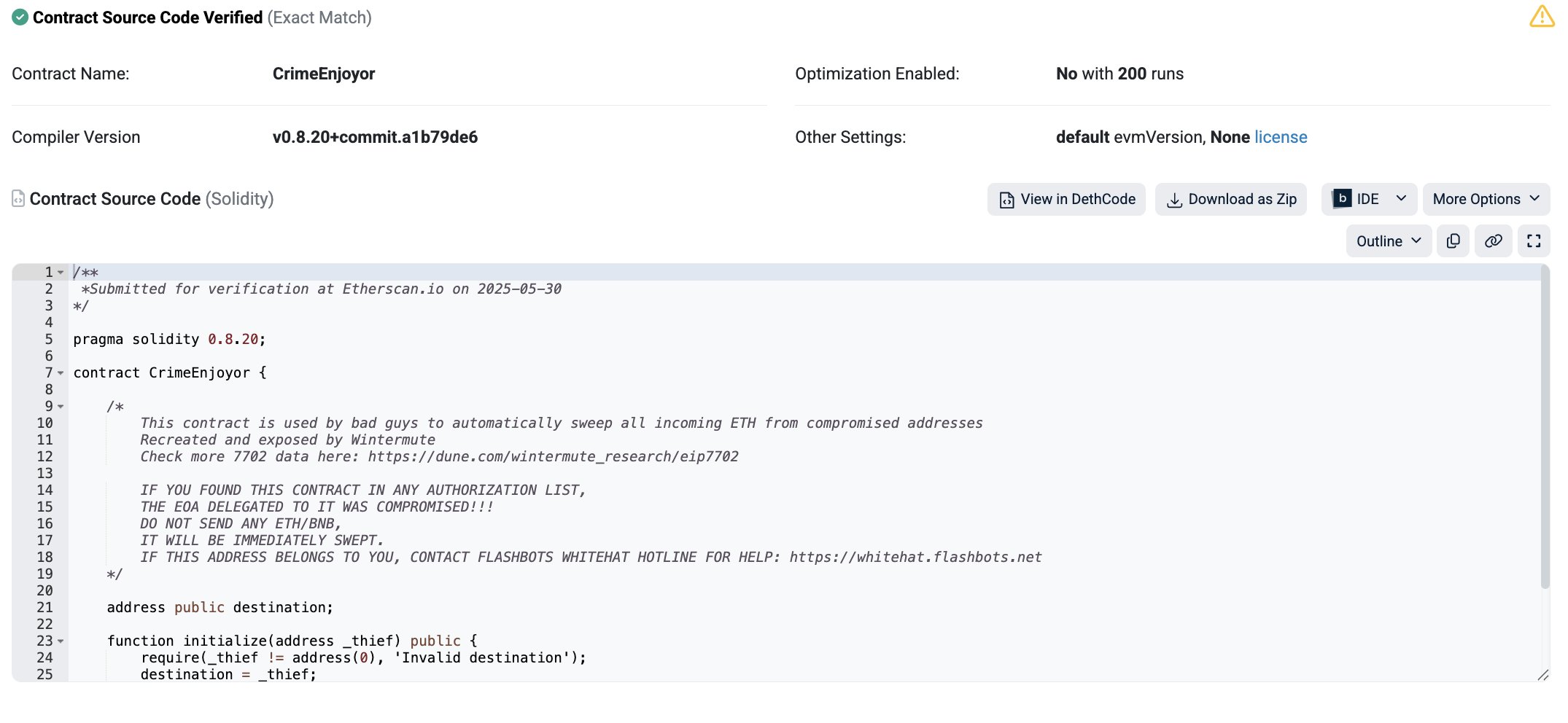
The tool of choice? A widely duplicated contract Wintermute nicknamed “CrimeEnjoyor.”
Here’s how it works:
Criminals deploy malicious contracts with simple bytecode, copy-pasted across thousands of instances. These contracts are designed to automatically sweep funds from wallets whose private keys have been compromised. Once these wallets receive ETH, the contracts instantly forward the funds to the attacker’s address.
Wintermute’s research, made available via a Dune dashboard, shows that over 97% of EIP-7702 delegations have been linked to these identical contracts.
“The CrimeEnjoyor contract is short, simple, and widely reused,” Wintermute noted on X. “This one copy-pasted bytecode now accounts for the majority of all EIP-7702 delegations. It’s funny, bleak, and fascinating at the same time.”
It’s Not Just a Smart Contract Problem
While EIP-7702 is the vehicle, the root cause remains compromised private keys.
Wintermute and other security experts emphasize that EIP-7702 isn’t inherently dangerous. Rather, it makes it easier and faster to steal funds once a wallet is compromised.
As security expert Taylor Monahan noted:
“It's not actually a 7702 issue. It’s the same issue crypto has had since day one: end users struggle to secure their private keys.”
EIP-7702 reportedly made it more efficient for attackers to clean out vulnerable wallets.
Real Losses: A $146,550 Example
On May 23, a user unknowingly signed several malicious batch transactions using EIP-7702. The result? A loss of $146,550, according to blockchain security firm Scam Sniffer.
These malicious transactions were linked to Inferno Drainer, a well-known scam-as-a-service provider that has been active in the crypto space for years.
An Inconvenient Truth for Ethereum’s Future
Wintermute took things a step further by reverse-engineering the malicious bytecode into human-readable Solidity code. This made it easier to identify and tag malicious contracts. They even verified the code publicly to raise awareness.
The code itself contains a warning in plaintext:
“This contract is used by bad guys to automatically sweep all incoming ETH. DO NOT SEND ANY ETH.”
But despite the warning, the contract remains effective. Users who don’t understand what they’re signing are at serious risk, especially when using unfamiliar dApps or tools that prompt them to delegate control under EIP-7702.
Another security firm, SlowMist, confirmed the growing threat. The firm urged wallet service providers to quickly adapt and support EIP-7702 delegation warnings.
"Wallet service providers should quickly support EIP-7702 transactions and, when users sign delegations, should prominently display the target contract to reduce the risk of phishing attacks," SlowMist said.
Pectra’s Other Features Now Overshadowed
The Pectra upgrade, which went live on May 7 at epoch 364032, also included two other major changes:
- EIP-7251: Raised the validator staking cap from 32 ETH to 2,048 ETH, improving efficiency for institutional validators.
- Performance and scalability improvements under the hood.
But due to the abuses of EIP-7702, these other upgrades have been largely overshadowed.
To date, more than 12,329 EIP-7702 transactions have been executed, most linked to delegations abused by sweeper bots.
So, What’s the Fix?
While EIP-7702 itself is opt-in, and not mandatory for basic transactions, the need for education, transparency, and wallet-level security improvements is more pressing than ever.
Users should:
- Never sign unfamiliar transactions without understanding the destination contract.
- Use wallets that display full contract information before confirmation.
- Treat any delegation requests with extreme caution, especially when bundled with multiple steps.
For developers, Wintermute suggests verifying contracts publicly and making dangerous patterns easier to detect. The firm believes that tagging malicious activity more aggressively can protect new users and reduce phishing risks.
Read Next...
Disclaimer
Disclaimer: The views expressed in this article do not necessarily represent the views of BSCN. The information provided in this article is for educational and entertainment purposes only and should not be construed as investment advice, or advice of any kind. BSCN assumes no responsibility for any investment decisions made based on the information provided in this article. If you believe that the article should be amended, please reach out to the BSCN team by emailing [email protected].
Author
 Soumen Datta
Soumen DattaSoumen has been a crypto researcher since 2020 and holds a master’s in Physics. His writing and research has been published by publications such as CryptoSlate and DailyCoin, as well as BSCN. His areas of focus include Bitcoin, DeFi, and high-potential altcoins like Ethereum, Solana, XRP, and Chainlink. He combines analytical depth with journalistic clarity to deliver insights for both newcomers and seasoned crypto readers.
Crypto Project & Token Reviews
Project & Token Reviews
Comprehensive reviews of crypto's most interesting projects and assets
Learn about the hottest projects & tokens